- Let's Connect!
- Email: support@securityboat.net
- Phone: +91 9175154999

As you recursively visit your local bank, there is a possibility that the bankers will recognize you by looking at you. Yes, we can call this a form of authentication. But as the world moves toward digitization, the methods of authentication are changing as well.
Now, we have to log in to our national bank’s website, and there are other methods of authentication that need to be completed. Authenticating your account allows you to confirm your identity with the site you have requested access to and reassures them that you are who you claim to be.
Now, let’s understand the concept of authentication in detail.
Authentication involves verifying a user’s identity before providing access to a particular system or resources. Authentication involves many different types of methods to verify the user including, using passwords, passcodes, Biometrics, Digital Signatures, OTP and many more.
Here is a simple example, after being logged in as a user “securityboat” change the cookie value from “securityboat” to “admin” as the application does not allow to recreate the account, we can bypass this in the manner given below.
Original Request
GET /dashboard HTTP/1.1
Host: target.com
[...]
Cookie: user=securityboat
Connection: closethis will result in the normal response
<span class="text text-warning">Logged in as securityboat! </span>Modified Request
GET /dashboard HTTP/1.1
Host: target.com
[...]
Cookie: user=admin
Connection: closethis will result in authentication failure, which will allow us to log in as an admin
<span class="text text-warning"> Logged in as admin! </span>To keep data secure, every company strives to use the best authentication process. A variety of authentication methods can be used to verify user identity. Some of them are listed below.
It enables users to log in to numerous applications with the same credentials. As a result of SSO, the user can log into multiple sites across different domains using the same set of credentials. Consider following example
GET /sso HTTP/1.1
HOST: target.com
User-Agent: Mozilla/5.0
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
If-Modified-Since:
If-None-Match: "317"
Cache-Control: max-age=0To bypass SSO you may use method alteration (changing GET to TRACE or GET to PUT) or response manipulation
HTTP/1.1 304 Not Modified ---------------> HTTP/1.1 200 Ok
Accept-Ranges: bytes
Age: 193835
Cache-Control: max-age=604800
Date:
Etag: "317"
Expires: Sun, 09 Jan 2022 14:39:09 GMT
Last-Modified: Thu, 17 Oct 2019 07:18:26 GMT
Server: ECS (dcb/7FA6)
Vary: Accept-Encoding
X-Cache:
Connection: closeIt uses different means of authentication. A one-time access code is sent to the user’s cell phone with the user’s name and password when the user logs in with the user’s name and password.This enhances security by adding an additional level of assurance during the authentication process.


This solution offers a variety of features such as support for self-service account management, consent and preferences management, and other authentication options.
Authentication and Authentication based Access control (ABAC) will both increase the security of data when used together. Based on the rich set of user data available through the security layers, the ABAC system makes easy use of policies and rules to lead and enforce access.
As soon as the system authenticated each user according to their role, it assigned some policies and limitations. Now the authorisation process begins.
Once the system has verified the user’s identity, it applies several policies or restrictions to them. Authorization is usually paired with authentication so that the server does not have to guess who the user is. Authorization is the process by which the system determines whether a particular user is able to access a requested resource or not. Here is a small example
POST /profile HTTP/1.1
Host: target.com
[...]
Connection: close
user%5Busername%5D=normal-user&user%5Bpassword%5D=124&submit=SubmitModified Request
POST /profile HTTP/1.1
Host: target.com
[...]
Connection: close
user%5Busername%5D=normal-user&user%5Bpassword%5D=124&submit=Submit&[admin]=trueThe two most common ways in which authentication mechanisms vulnerable are:
There is no adequate protection against brute-force attacks due to weak authentication mechanisms.An attacker can bypass the authentication mechanism entirely due to logic flaws or bad coding in the implementation. This is called “broken authentication”.
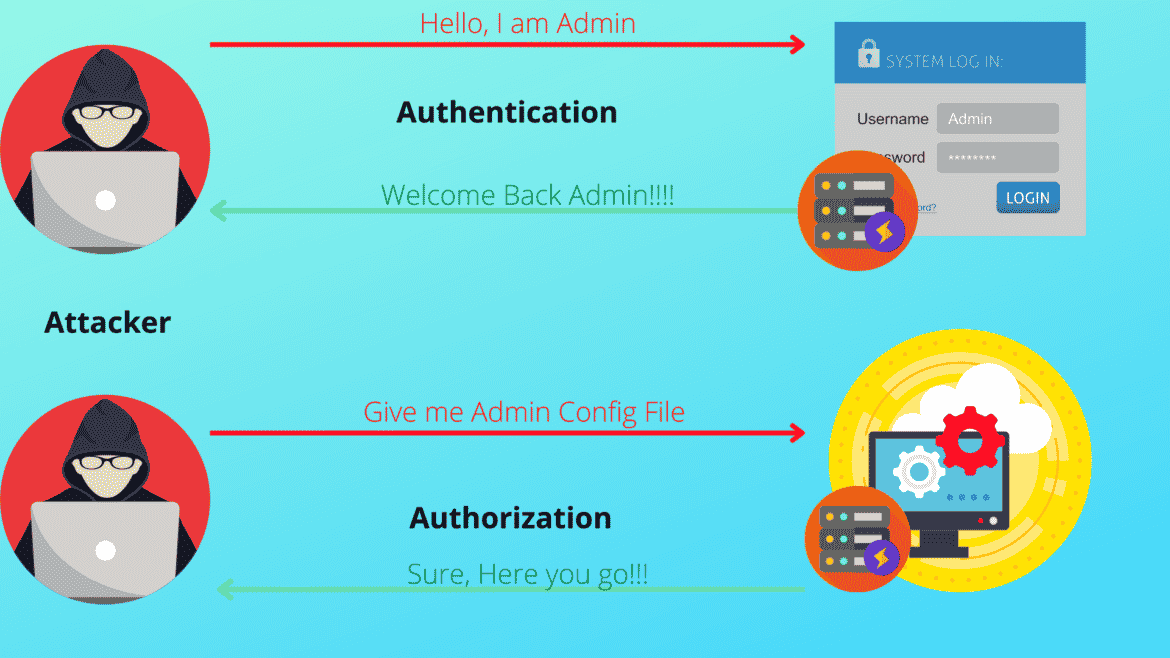

There will often be logic flaws in web development that result in websites acting unusually, which may or may not be a security issue. Nevertheless, since authentication is such a critical aspect of website security, the probability that the login process is flawed puts the website at risk for security breaches.
A two-factor authentication is an extra form of authentication used in conjunction with the user’s password. In addition to a text message authentication code, authenticator applications, fingerprints, or face recognition can also be used as a second layer of authentication. A two-factor authentication method falls under multi-factor authentication. In the case of multi-factor authentication, the user is required to identify himself/herself in more than two different ways.
Let’s understand how it works in practice. Using traditional session management bypass 2FA
Bypass
Because 2FA is frequently not implemented on the system’s login page after a password reset, attackers use the password reset mechanism in this instance. What does it look like in practice?
The attacker requests the password reset token. The attacker uses the password reset token.
Using this method, attackers can bypass the two-factor authentication in certain platforms where the architecture of the site or platform makes it possible.
Mainly there are two types of privilege escalation.
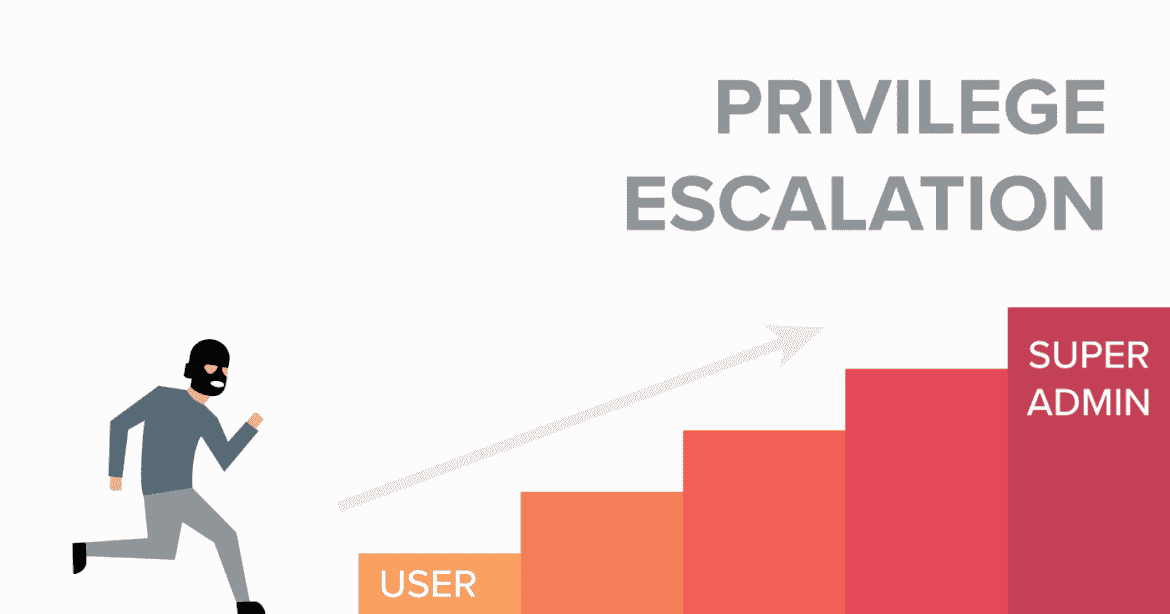

Horizontal privilege escalation is the process by which a user gains access to the same resources as another user of the same privilege level. This is a little strange, isn’t it? An attacker can identify a weakness in an application that allows him to gain access to other users’ information when the application is poorly designed.
Vertical Privilege Escalation is performed when an attacker attempts to gain access to additional permissions by exploiting a compromised account. For example, an attacker takes over a regular user account on a network and attempts to gain administrative permissions or root access.
Here is an example,
An attacker can escalate their privilege by changing the username parameter to the admin in the following request. Changing this request from
POST/login HTTP/1.1
Host: target.com
User-Agent: Mozilla/5.0
Accept: text/html,application/xhtml+xml
Accept-Language: en-US, en: q-0.5 Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 67
Origin: https://sub.target.com
Connection: close
Cookie: session-something
Upgrade-Insecure-Requests: 1
username=test¤t-pass=test%40111&new-password=new%40123to
POST/login HTTP/1.1
Host: target.com
User-Agent: Mozilla/5.0
Accept: text/html,application/xhtml+xml
Accept-Language: en-US, en: q-0.5 Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 67
Origin: https://sub.target.com
Connection: close
Cookie: session-something
Upgrade-Insecure-Requests: 1
username=administrator¤t-pass=test%40111&new-pass=new%40123This was an example of vertical privilege escalation.
It refers to the process of gaining access to restricted areas of a website directory without authorization.
By directly navigating to the URL of a website, an attacker can forcefully browse through its contents. An attacker can use Brute Force tactics to search for unlinked contents in the domain directory, such as temporary directories and files, as well as old backup and configuration files. Web applications and operational systems may store sensitive information regarding source code, credentials, internal network addresses, and so forth; this may be considered valuable information for the attack.
https://www.target.com/authorize/It is also possible that the attacker may also gain access to a database file by directly navigating to the particular path.
https://www.target.com/configuration/Here, the attacker gets access to all the configuration files for the web application. There may be some files in those locations that contain sensitive information, such as database access passwords.
http://www.target.com/user/account
http://www.target.com/admin/panelis another such example.
Objects are at the core of the problem. When you create a program, you think about objects first, and the generated code follows on from them. A customer account may consist of anything from like bank details or some transaction information. This type of object is normally identified since it needs to be addressed directly, which could cause problems since we must always verify whether a user can access it.
A web application’s authentication methods can be bypassed or captured by attacks exploiting this type of weakness.
Insecure Direct Object References (IDOR) occur when an application grants direct access to objects based on the user’s input. Because of this vulnerability, attackers can bypass authorization and access resources in the system directly, such as database records or files. By modifying a parameter used to directly point to an object using an insecure Direct Object Reference, an attacker can bypass authorization and gain access to resources directly. Using the Human eye to detect and observe from where the request is being made and how it functions in the web application certainly makes it more likely to find these vulnerabilities. In most cases web applications expose the user_ids or user_keys in the request or response, this enables the attacker to access or modify the data present for a specific end user.
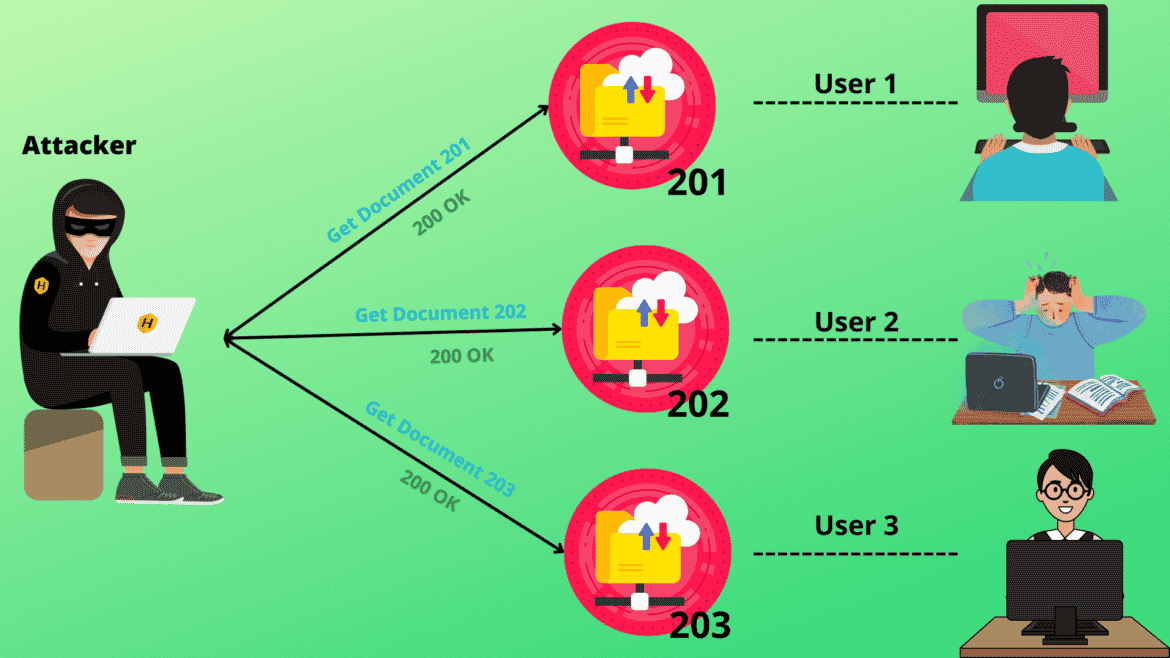

To understand this thoroughly,
https://vulnrable-website.com/update_profile?id=99 is the request made by the web application to update the profile of end-user 99. The update in the URL specifies the function and parameter “id” is responsible for detecting valid and authenticated user account. What if we change this request from
https://vulnrable-website.com/update_profile?id=99 to
https://vulnrable-website.com/update_profile?id=100This exposes the unauthorized data to the attacker and carries out unethical actions if the parameter “id” is used with direct object references. Here web server and application are completely dependent upon the user input which is used directly to refer to the objects head-on. This was a simple demonstration to understand IDOR better.
Go to Idor in order to understand it thoroughly.
Authentication and authorization hacks seek to take resources by impersonating the client. A hostile actor may be able to access unlawful content, edit or remove content, execute tasks, and even take full control of site management if the assault is successful. Whenever an intruder has circumvented authentication or accessed the account his entry further into a customer’s profile, they gain control of all of the data and capabilities of that account. Faulty authentication has the functioning effect of the solution that is unable to authenticate the person executing an action request.


is amongst the major impact which the attacker does after the access.
An attacker might take complete control of the programme and perhaps obtain access to the sensitive structures if they can breach a strong identity, including a super user. The attack’s harm is solely limited by the privileges provided to the spoofing victim after this degree of compromise has been established. An intruder might access confidential material by reading it straight from unrestricted data storage or by using improperly secured authorized functionality.


Authentication and Authorization flaws are frequently undiscovered by automated security scanners, necessitating extensive study by security experts. The authentication vulnerabilities include single-sign-on, multi-factor authentication, weak login function and many more occurring due to improper handling of passwords, brute force protection, enumerations and poor session management. Insecure direct object references, privilege escalation, and forced browsing are all examples of authorization, which refers to an attacker granting oneself the ability to do operations that are intended to be performed with a specific degree of permission. This type of activity is mostly caused by the use of sequential or predictable reference IDs. The human eye is essential in finding these flaws. Employees abusing their granted powers is perhaps the most serious threat connected to authorization. Some solutions to mitigate these problems include brute force protection, a valid password complexity, keeping HTTP stringent rules, preventing enumerations, and verifying password reset codes. Authorization issues may be mitigated by using an Indirect Reference Map, imposing access control, and not disclosing sensitive account information. As a result, authentication and authorisation issues might put end user’s and super users’ web application security at risk.
1.Authentication Bypass by bugcrowd
2.Authentication bugs by portswigger
3.Broken Authentication by packetlabs
5.Privilege escalation by invicti.com
6.Broken Authorization by secureflag
7.Most common authorization vulnerabilities by goteleport
8.5-ways-to-bypass-two-factor-authentication by hoxhunt
Here are some labs for these vulnerabilities.