- Let's Connect!
- Email: support@securityboat.net
- Phone: +91 9175154999









Ghidra is a powerful software reverse engineering tool, initially developed by the National Security Agency (NSA) and subsequently released as open source. It provides a suite of capabilities for analyzing compiled code, Ghidra proves indispensable for security researchers, software developers, and professionals exploring the inner workings of binary executables. Particularly valuable in the realm of IoT security, Ghidra empowers experts to navigate the complexities of embedded systems, ensuring a robust approach to securing connected devices
Key Features:
In this section, we will exclusively explore the Ghidra Code Browser, Debugger, and Emulator. This focused exploration aims to provide users with a direct understanding of these core tools within the Ghidra environment for both static and dynamic analysis.
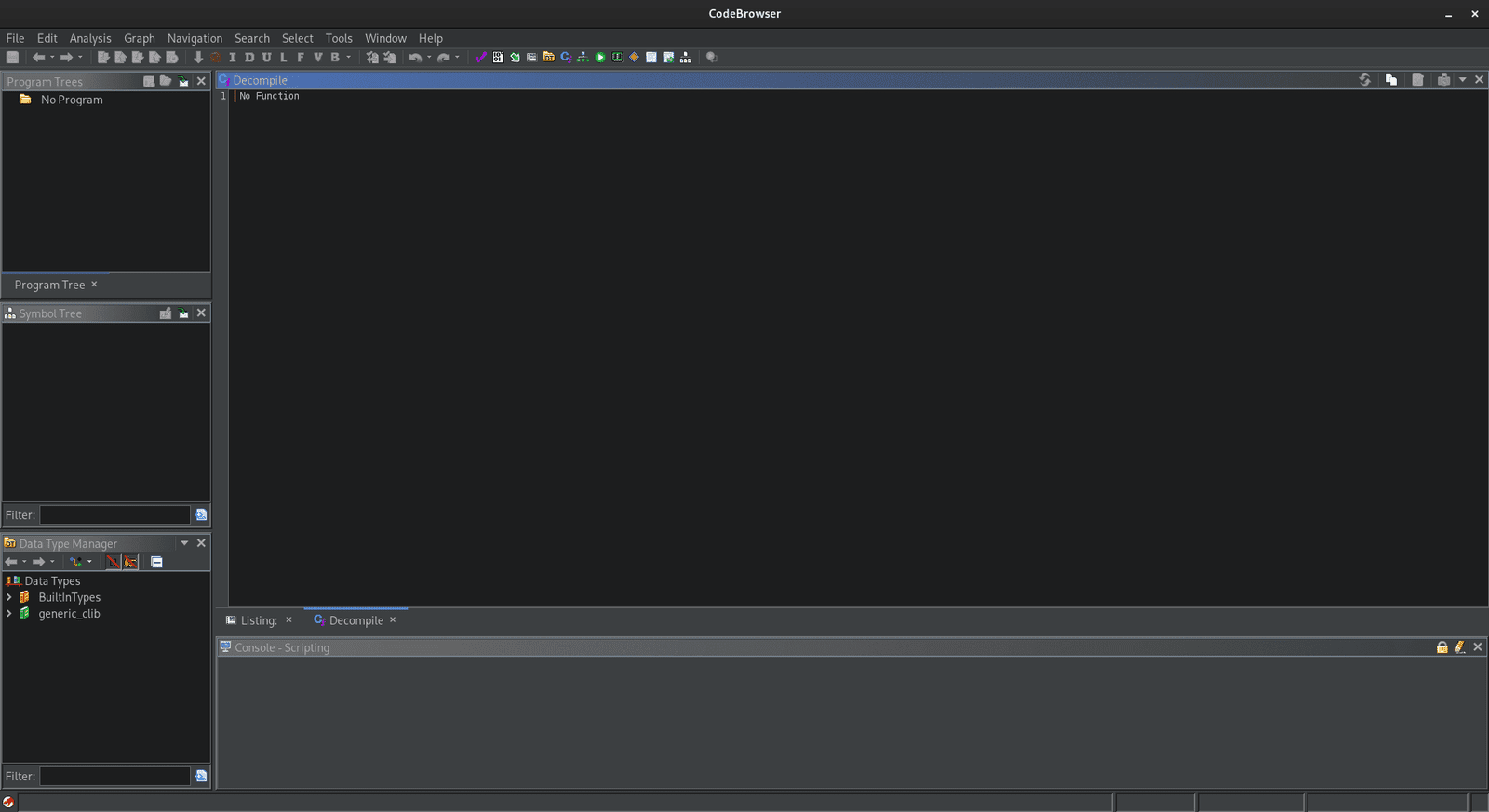
The Ghidra Code Browser is the core interface for examining and analyzing binary code. It presents a comprehensive view of disassembled or decompiled code in the central listing panel, allowing users to navigate through functions and understand the logic of the program. The Code Browser includes features such as the Function Graph, aiding in visualizing control flow. With integrated tools like the Data Type Manager and Symbol Tree, users can efficiently manage data types and navigate symbols. The search bar and navigation options enhance the ability to locate specific addresses or functions quickly. This interactive and user-friendly interface serves as the primary workspace for conducting detailed code analysis within the Ghidra framework.
The Ghidra Debugger is a powerful tool for dynamic analysis, allowing users to investigate the runtime behavior of binary code. Integrated seamlessly into the Ghidra interface, the debugger enables users to set breakpoints, inspect and modify memory, and step through code execution. It supports various debugging features, including register and memory views, call stack analysis, and breakpoint management. The debugger is compatible with external debuggers like GDB, providing flexibility for both static and dynamic analysis within the Ghidra environment. This feature-rich tool enhances the reverse engineering process by enabling users to understand and interact with the binary’s execution flow in real-time.


The Ghidra Emulator is a crucial component for dynamic analysis, providing a simulated execution environment within the Ghidra framework. It allows users to emulate and execute binary code, facilitating the understanding of program behavior without running it on the actual target hardware. Integrated into the Ghidra Code Browser, the emulator provides valuable insights into the runtime execution flow, allowing users to trace code paths, identify potential vulnerabilities, and analyze the impact of specific instructions. With features such as register and memory views, users can closely examine the state of the emulated program during execution. The Ghidra Emulator is a versatile tool that complements static analysis, offering a comprehensive approach to reverse engineering by combining both static and dynamic perspectives.


In this section, we’ll engage in a hands-on demonstration using Ghidra. We’ll dive into the fascinating world of reverse engineering using a CrackMe challenge. A CrackMe is a specially crafted program designed to test and improve your skills in cracking software protection. We’ll leverage the powerful capabilities of Ghidra to dissect and understand the inner workings of this CrackMe file. Step-by-step, we’ll explore Ghidra’s Code Browser revealing how this open-source tool unveils the secrets hidden within executable binaries. Get ready to crack the code and witness Ghidra in action, providing insights into the art of reverse engineering.


After the file downloaded unzip it using the password “crackme.one”. Unzip the rev50.zip in that folder to you will get the challenge rev50_linux64-bit executable file.














undefined8 main(int param_1,undefined8 *param_2)
undefined8 main(int param_1,undefined8 *param_2)
int main(int argc, char *argv) // C main function standard syntax


* argv” is not treated as array instead it is treated as a part of function so we need to modify it as follows in order to workint main (int argc, char ** argv)



size_t sVar1;
size_t and name sVar1. Now lets check next lineif (argc == 2)sVar1 = strlen(argv[1]);sVar1 variable if (sVar1 == 10) {
if (argv[1][4] == '@') {
puts("Nice Job!!");
printf("flag{%s}\n",argv[1]);
}
else {
usage(*argv);
}argv[1][4]
argv[start][end]
// The starting index is 0 by default but here it's given to 1 so from the 1 to 4 it gives us the 5th letter in string.argv[1].usage(*argv) you will get following code which is executed in “else” block.



Congratulations! You’ve successfully reverse-engineered the CrackMe challenge.
In summary, our exploration into Ghidra’s fundamentals and practical application on a real-world CrackMe challenge has provided valuable insights into the realm of reverse engineering. Whether you’re just starting or aiming for expertise, this guide equips you with essential skills, guiding the way for a confident journey into the world of code analysis. Stay tuned for more exciting revelations as you continue your reverse engineering adventure!