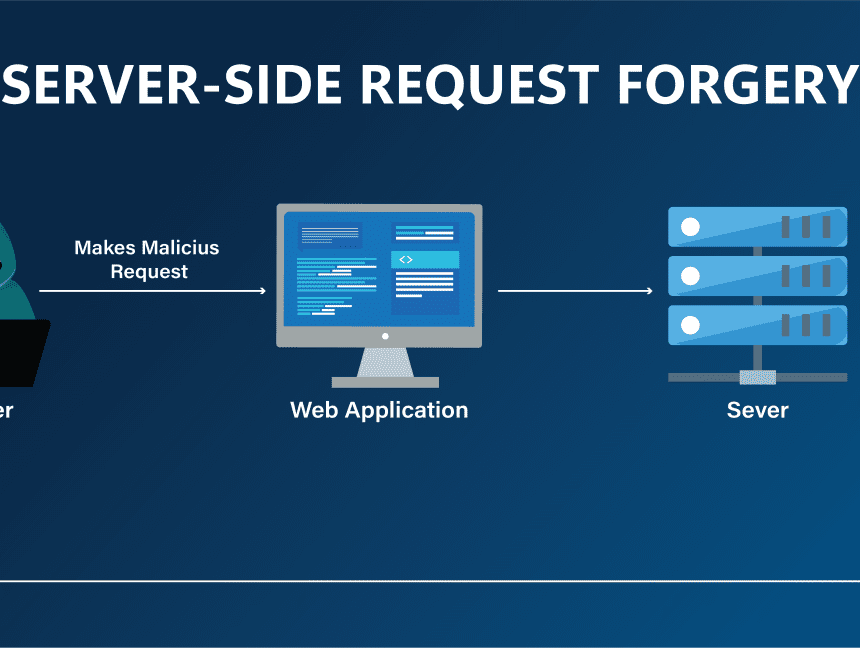
Server Side Request Forgery
Server Side Request Forgery is a web security vulnerability in web applications in which the user can forge server request to access unintended location usually these are request made to internal-only services within the organization’s infrastructure.