Hello everyone, today we will do an analysis of SSTI vulnerabilities that were found on HackerOne. SSTI stands for Server-Side Template Injection which is a vulnerability that occurs when an application allows user-controlled data to be embedded directly into server-side templates. Researchers can exploit this vulnerability to execute arbitrary code or gain unauthorized access to the server.
Template engines generate dynamic content by combining predefined templates and data, simplifying the separation of logic and presentation in applications. They provide a convenient way to insert and manipulate data within templates, facilitating code reuse and maintainability.
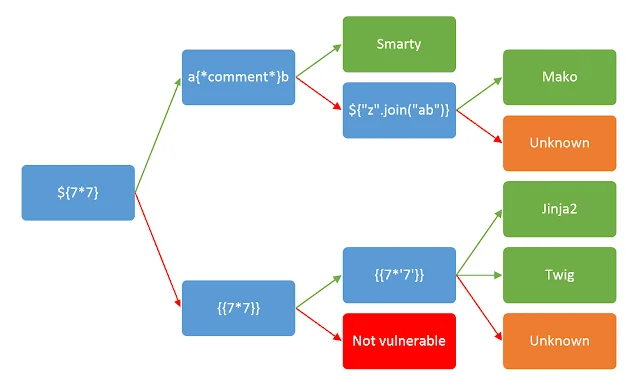
Moving further about the first report, the researcher got the functionality to invite another user via mail. When the researcher sends an invite link to another new user the researcher’s name appears in the invite mail. So researcher edited his name in the profile section and inserted {7*7} and sent new invite mail to the new user. After the new user opened the invite mail, he got an error that disclosed that the template engine is a smarty. Smarty is a popular template engine for PHP, known for its flexibility and extensive features.

After that, the researcher constructed the below given payload
{php}$s = file_get_contents('/etc/passwd',NULL, NULL, 0, 100); var_dump($s);{/php}
Explanation of the payload:
The PHP function `file_get_contents()` is used to read the contents of the file located at `/etc/passwd`. The parameters `NULL, NULL, 0, 100` are provided to specify that the function should start reading from the beginning of the file and retrieve the first 100 bytes. The retrieved content is stored in the variable `$s`.The `var_dump()` function is used to display information about the variable `$s`, including its content, data type, and length. It’s important to exercise caution when working with sensitive files like `/etc/passwd` to prevent unauthorized access and ensure proper security measures are in place.
The researcher put that payload in his name field which was vulnerable to SSTI. As the researcher sent the invite to another user, the invited user can see the /etc/passwd file as shown below.
The second report outlines a Remote Code Execution vulnerability found on the rider.uber.com website. By injecting the SSTI payload in the profile name field, the researcher can execute arbitrary code. The researcher detected the template engine which was Jinja. Jinja is a templating engine for Python that is widely used in Flask and other Python web frameworks. The vulnerability is limited by a length constraint but still allows for the execution of certain Python code.
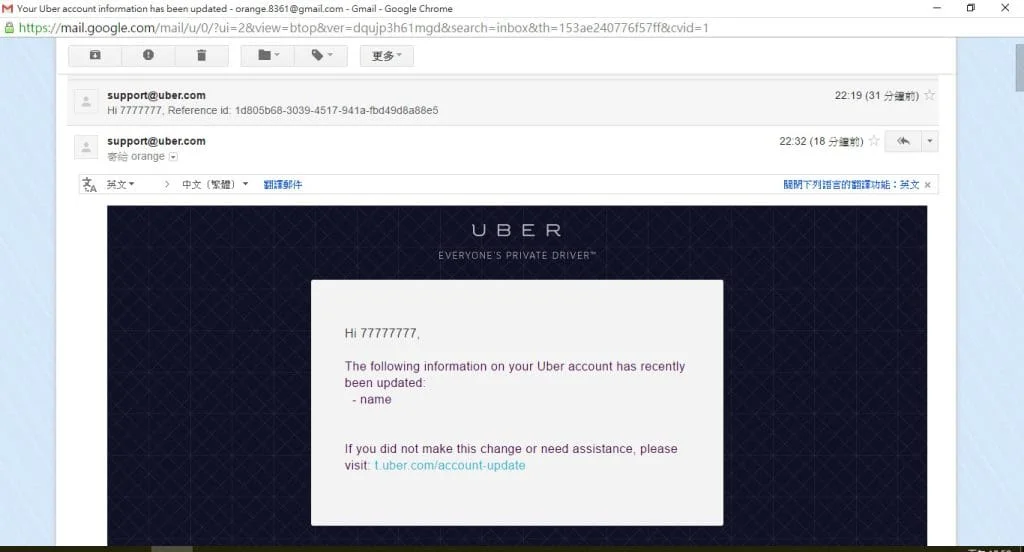
During testing of the rider.uber.com website, a Remote Code Execution vulnerability was discovered. By changing the profile name to {{ ‘7’*7 }} and researcher got a profile updation email which is sent from support@uber.com. In the body of the email, the name is displayed as ‘7777777’. As shown in the below figure.
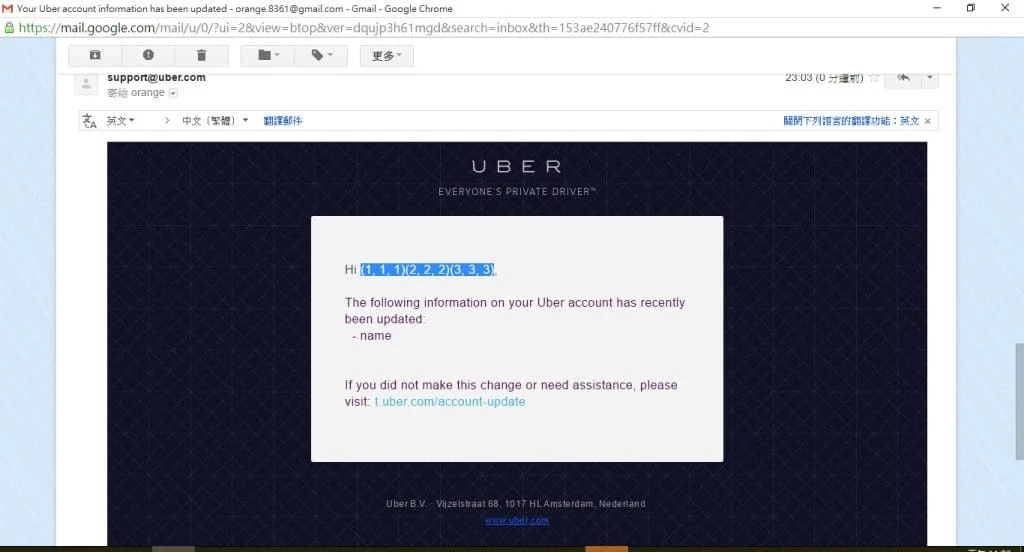
Although there is a length limitation imposed on the payload, it is still possible to “write” Python code within the “name” field. The following payload can be used to execute code within the context of the application:
{% for c in [1, 2, 3] %}{{ c, c, c }}{% endfor %}
Explanation of the payload:
{% for c in [1, 2, 3] %}: This starts a loop where the variable c iterates over the values in the array [1, 2, 3].
{{ c, c, c }}: This part of the code is a template variable that displays the value of c three times, separated by commas.
{% endfor %}: This signifies the end of the loop.
It should be noted that the length constraint may limit the complexity of potential exploits.
The third report details the discovery of a security vulnerability within the Shopify Return Magic app, specifically related to the Email Workflow feature. This feature allowed shop owners to customize email templates using variables. During participation in a HackerOne event organized by Shopify, the researcher identified a potential vulnerability involving remote code execution (RCE) through handlebars template injection.
Initially, the researcher mistakenly believed that the template engine used by Shopify was Mustache. Consequently, he attempted to find Mustache template injection techniques but was unsuccessful. Eventually, it was discovered that the template engine in use was Handlebars. Although Handlebars is designed to mitigate template injection attacks, the researcher discovered a means to access the function constructor and invoke functions by employing the {{this.constructor.constructor}} syntax.

Further experimentation revealed that the researcher could exploit the Handlebars template engine through the utilization of the built-in “with” helper. By manipulating the template context using the {{#with}} syntax, he could execute code with the assistance of the function constructor. However, challenges arose in passing parameters to the constructor due to the template compiler’s treatment of function calls.
Further experimentation led the researcher to a solution involving the modification of the Object.prototype.toString() function using Object.prototype.defineProperty(). This technique enabled the creation of a string that could be controlled by the user, with its toString() method bound to a function containing the desired code. By overwriting Object.prototype.toString() with this customized function, the researcher achieved the ability to execute code remotely.

Mitigations
To prevent Server-Side Template Injection (SSTI) vulnerabilities, it is crucial to implement effective preventive measures. Firstly, input validation should be performed rigorously, carefully validating, and sanitizing user-controlled data before incorporating it into server-side templates. Secondly, contextual output encoding must be applied to user-generated content rendered within templates to treat user input as data and prevent its execution as code. Additionally, template engine configurations should be optimized to enforce strict security measures, disabling, or restricting potentially dangerous features. Following the principle of least privilege, limiting access and permissions to sensitive resources can also mitigate the impact of an SSTI vulnerability.
References
https://workbook.securityboat.net/resources/web-app-pentest/server-side-template-injection-ssti
https://hackerone.com/reports/125980



