Empower your security strategy, uncover vulnerabilities, and mitigate risks with
expert-guided, cutting-edge Penetration Testing services.








Gathering critical data to identify vulnerabilities in the target
system for effective testing.

Simulating real-world cyberattacks to identify exploitable
vulnerabilities in your systems.
Providing detailed reports on vulnerabilities, risks, and
remediation recommendations.

Tailored and general fixes implemented to resolve identified
vulnerabilities effectively.

Retesting after remediation to confirm vulnerabilities are
resolved and systems are secure.

Web application pentesting entails exploiting vulnerabilities to evaluate security posture and protect against possible cyber threats in Web application. It exposes
flaws and enhances the website’s defence systems.
Android Security assists in examining full mobile applications to find and eliminate potential vulnerabilities, ensuring robust protection against cyber threats.
Immediate response to security breaches, containing threats, mitigating impact, and preventing further compromise.
Explore real-world case studies showcasing our cybersecurity solutions
in action. Discover how we’ve effectively helped businesses enhance
their security and safeguard their operations.
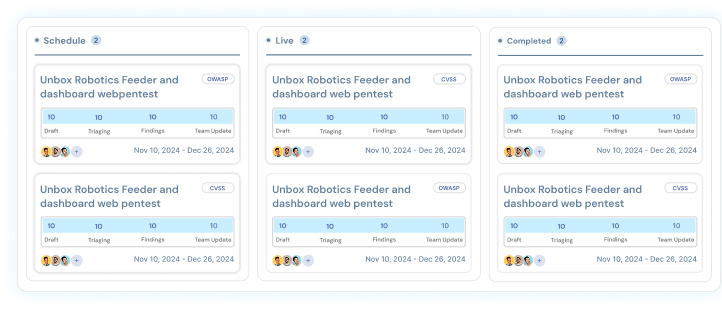
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform
The Challenge Our penetration testing team was tasked with a Web application penetration test for an undisclosed Digital Vault Platform

Address: 4th floor M- Arch Center,
Pashan-Sus Road, Baner, Pune 411021
Email: support@securityboat.net
Phone: +91 9175154999
Latest resources sent to your inbox weekly
Latest resources sent to your inbox weekly
Copyright @2025 SecurityBoat. All Rights Reserved by SecurityBoat.